CSIT Aug 25 Mini Challenge
This blog post talks about CSIT Aug 25 Mini Challenge.

Introduction
Happy National Day!! It has been a few months since the previous release of a CSIT Mini Challenge, lets tackle this one! There are 4 parts to this challenge (as extracted from their completion page). Disclaimer: As of today, the challenge is still available! Please attempt it before looking at the walk through :)
💻 [Challenge 1] DevOps
By meticulously debugging and resolving issues in a fracture repository, you have demonstrated proficiency in VCS and enabled the restoration of a Continuous Integration pipeline. This gives you a taste of resilient software development and delivery.
🔍[Challenge 2] Cryptanalysis Fundamentals
Analyzing clues from seemingly innocent data and piecing the clues together demonstrates a level of Pattern Recognition and Logical deduction which are crucial for Data Analysts and Cyber Forensic to think outside of the box to unearth the hidden information.
🔐[Challenge 3] Software Security
To protect against sophisticated web-based attacks, Web developers must understand and mitigate vulnerabilities in web applications. As misconfigured authentication mechanism or Client-Side scripting & DOM manipulation can result in exposure of attack vectors into a system through the web app.
🛡️[Challenge 4] Digital Forensics & Intelligence Integration
By synthesizing clues from multiple sources and analyzing transportation data to extract hidden codes, you have demonstrated the investigative skills essential for Cyber Intelligence operations. This multi-source correlation approach mirrors how Security Analysts uncover hidden threats in critical infrastructure systems.
Walkthrough
This month's challenge can be found here. It may not be up if you're reading this a few months later.
Challenge 1
Lets begin. When navigating to the first tab, the hint reveals that theres a magnifying glass on this page that leads to the challenge page. However, as my browser as a POP-UP blocker enabled, it seems the .js script failed to load. After disabling the blocker, I am able to see the icon.
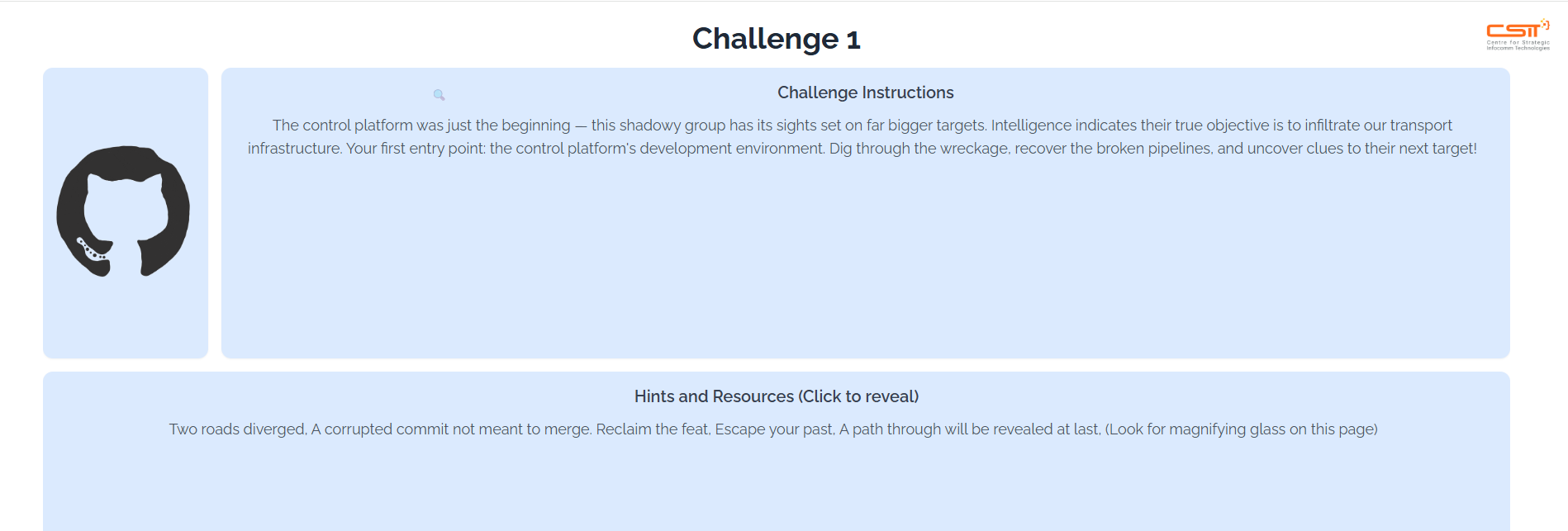
The first challenge is a devops-ish challenge that requires you to fix, merge, reorder, delete certain commits from certain branches.
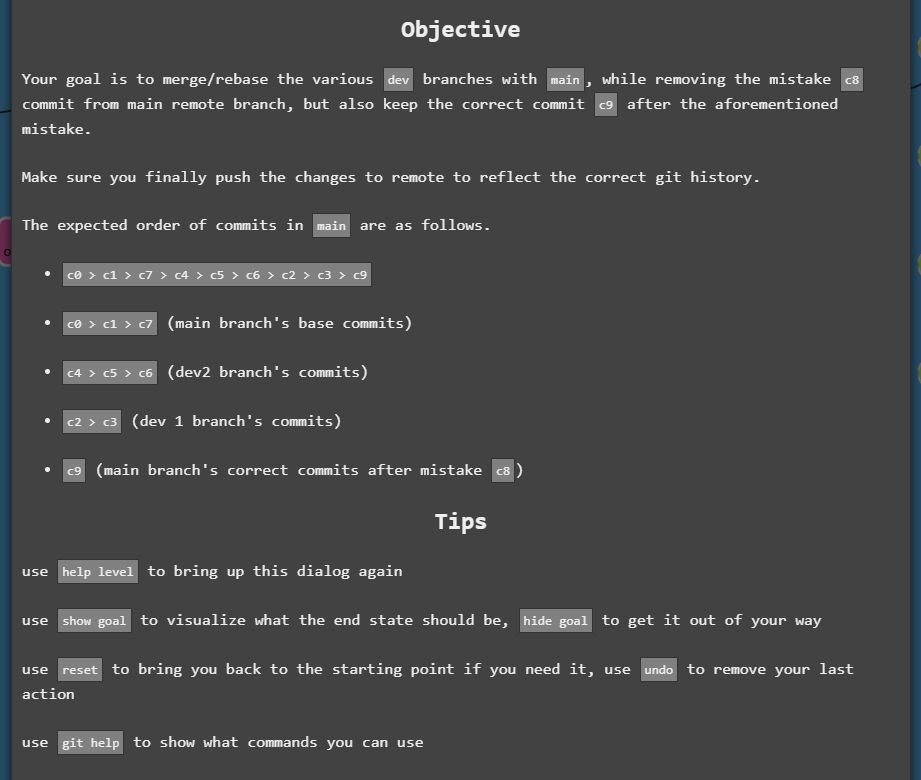
The model answer in the shortest amount of steps (7 steps) is listed below. This is defintely not the ONLY way to solve this. So if you manage to arrive at the same endpoint in a different variation of steps, thats fine too. I will not go into detail as to what each command means because the animation provided by the GUI in challenge 1 really does a amazing job at showing what happens when you enter each command. It even shows the head pointer.
git reset c7
git rebase main dev2
git rebase dev2 dev1
git checkout main
git merge dev1
git cherry-pick c9
git push --force
*btw if you're really stucked, you can enter `show solution` and the console will give you the answers!*
After a successful series of commands, you'll arrive at this pop-up with the flag.
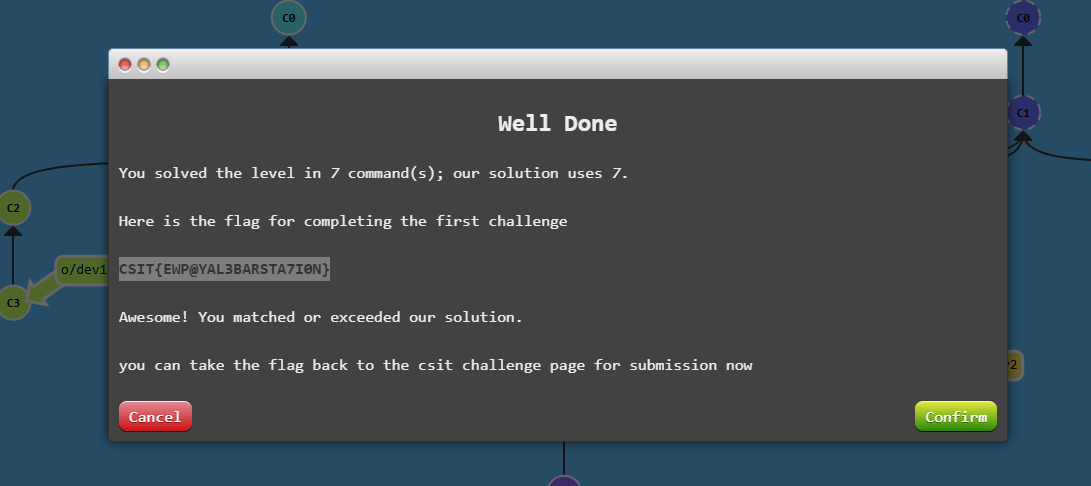
Challenge 2
This section has a hidden icon that downloads a txt file. If you open the txt file, you'll see a bunch of jibberish icons. At the top of the file, there should be a header with "PK". A quick Google search tells me that b'PK\x03\x04' means the file is actually a ZIP archive, not a WAV at all, as one would expect from a audio file.
Upon unzipping, there are two WAV files and one README file to tell you how to join the two flags to submit. The first WAV file sounds like the tone when you key numbers in your phone. This tone is called DTMF which stands for Dual-Tone Multi-Frequency, is a signaling system used in telecommunications where each digit on a telephone keypad is represented by a unique combination of two audio tones.
Here are some useful websites that you can use to help decode the wav files. The heavy lifting is already done by these apps, but if you want to learn what goes on behind decoding these audio files, you'll have to do a little research on your own.
- https://pypi.org/project/dtmf/
- https://dtmf.netlify.app/
- https://morsecode.world/international/decoder/audio-decoder-adaptive.html
- https://github.com/ribt/dtmf-decoder
- http://dialabc.com/sound/detect/index.html
For the DTMF audio file, I forked ribt's github project "dtmf-decoder" and added a decoder with the keypad mapping. Please free feel to use it at my github page here.
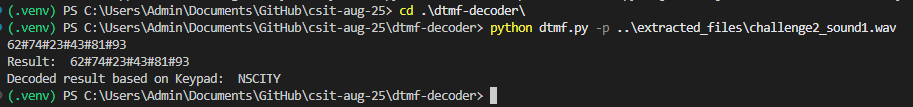
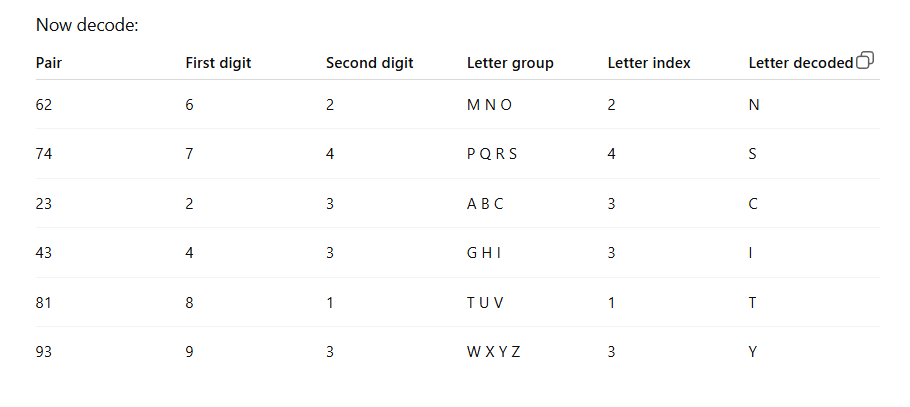
I have included a table below (kindly generated by ChatGPT) to help explain what the pair of digits followed by the # means. This logic is incorporated into the keypad mapping addition to the original github project. You can find this modified version from the link above. I have submitted a pull request to the main project but I doubt its being actively maintained now.
For the morse code audio file, I used one of those webapps for a solution. The decoded text is your Flag 2. "H@LLS7AT10N".
Join the two partial flags found and you'll get Challenge 2's flag.
Challenge 3
This section requires you to generate a valid JWT token to get the flag. JWTs are primarily used for authentication and authorization in web applications and APIs. The developer console reveals some hints... Something important to note is the "secret-key" mentioned in the console.
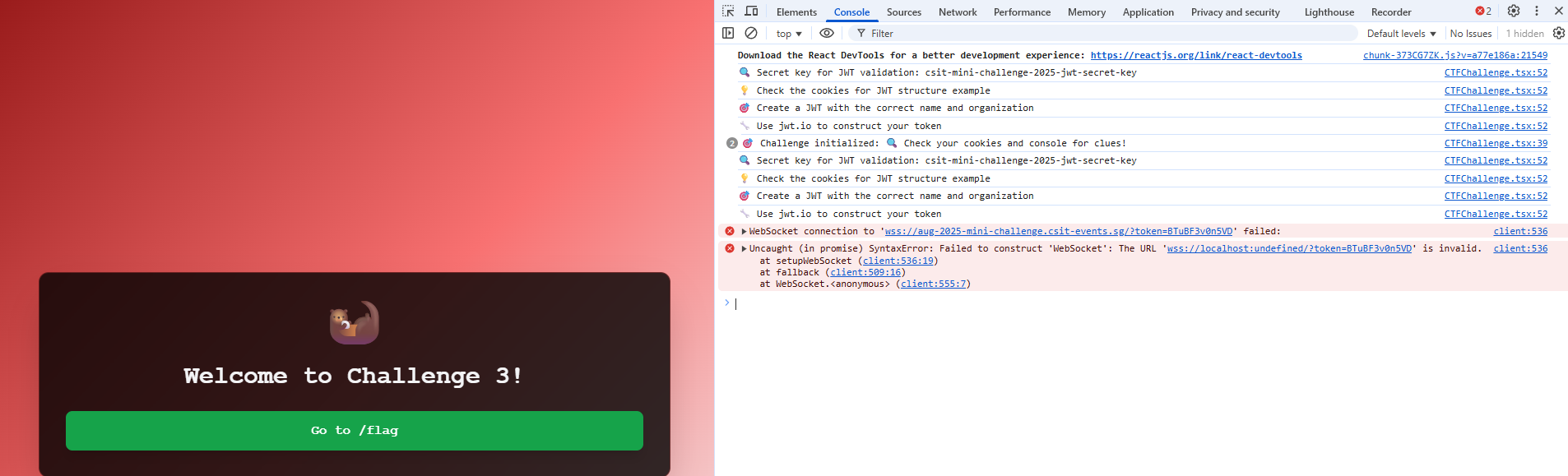
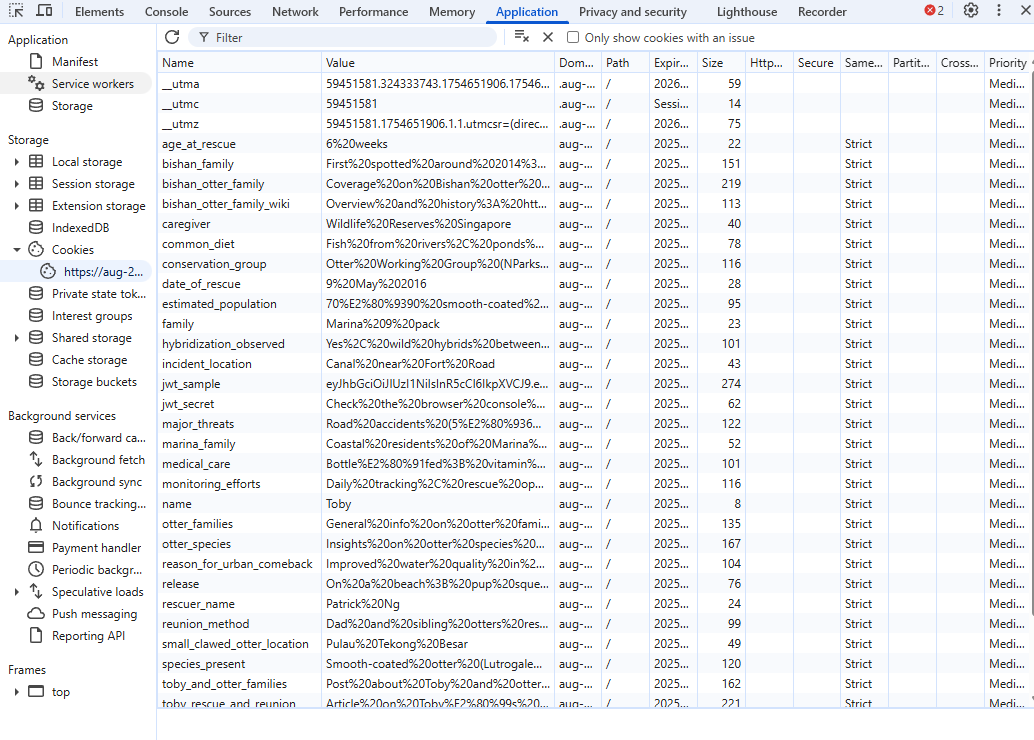
To generate a valid JWT token, we first need to know what format a normal JWT token has. The cookies has a jwt_sample parameter with 3 dots - which resembles a JWT token. Using jwt.io we are able to see exactly what payload this token has. If you recall, these fields are found within the cookies! The time in unix can just be a valid timeframe.
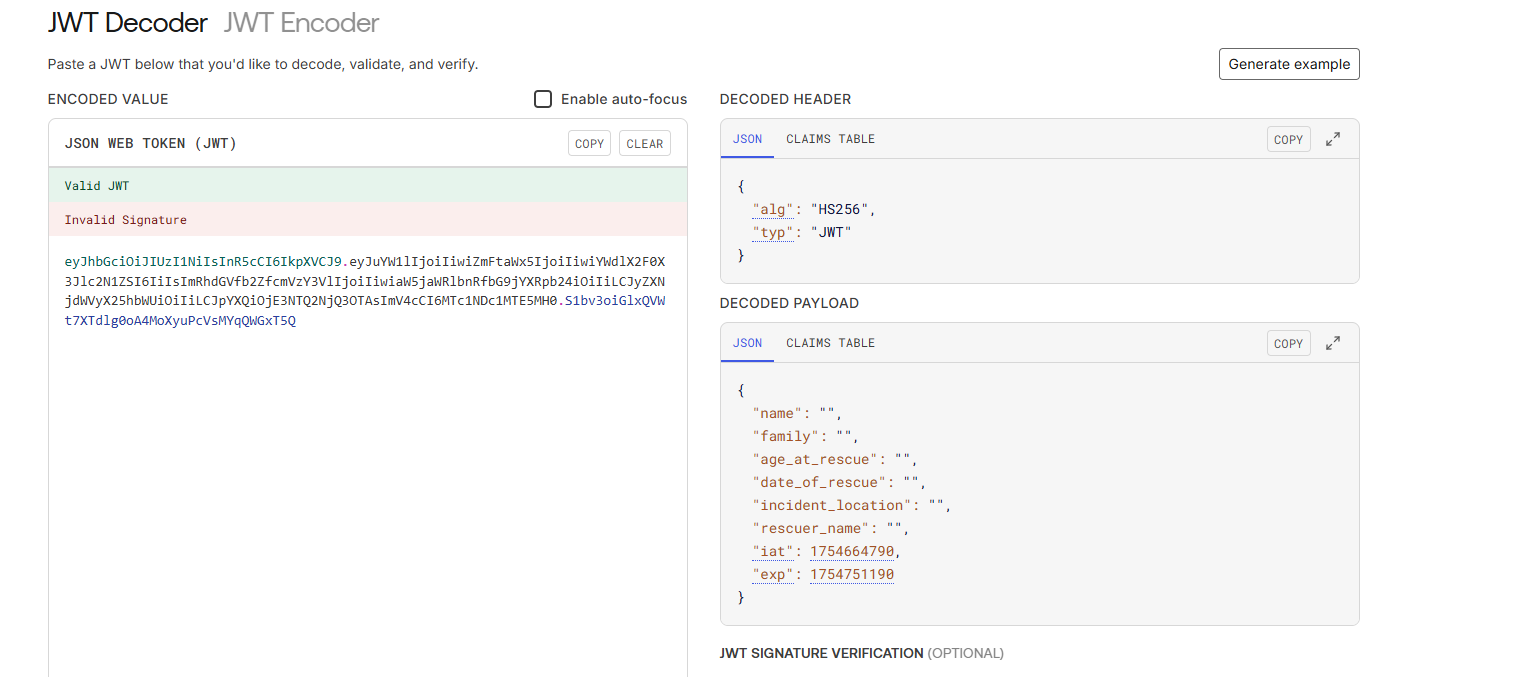
After you've identified the correct information, populate the JSON and throw it back into jwt.io. Remember to include the secret key.
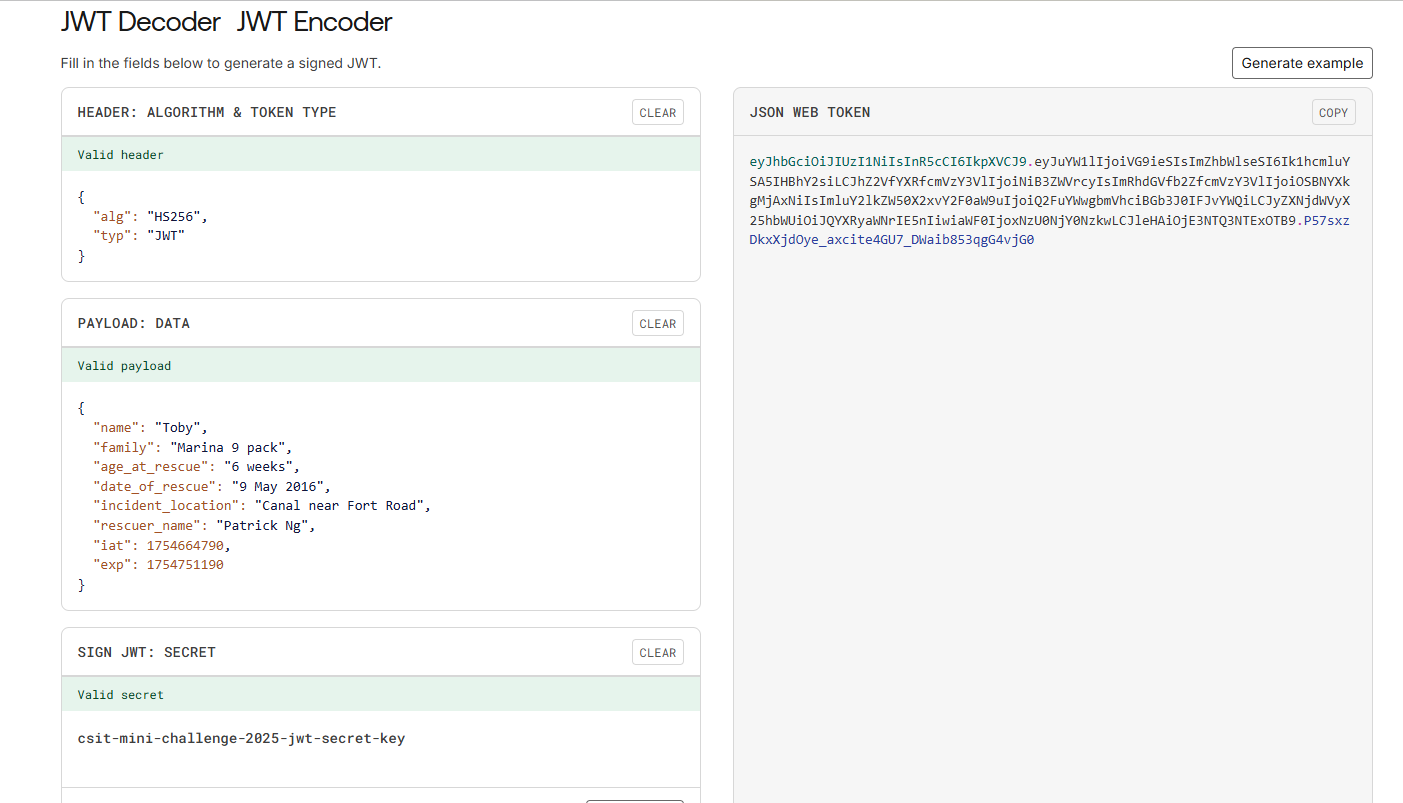
Take this token and input it into challenge 3 submission box, you'll get back the flag.
Challenge 4
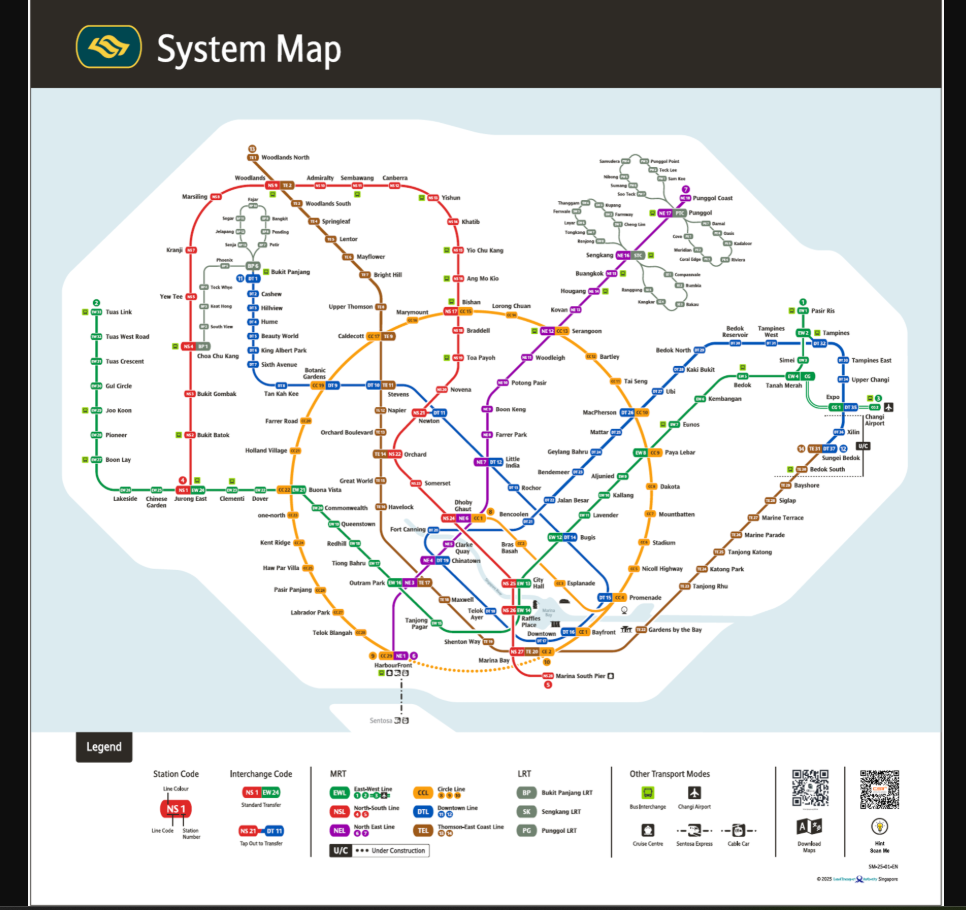
This is probably the easiest section yet haha. They provided a MRT map with a obviously edited QR code at the bottom right side.
Scanning the QR code takes to you a hint page that tells you how to submit the final flag based on the previous 3 challenge findings. There were two versions of this hint page, one was in the first week of Aug, and the other captured around 18 Aug. I presumed that too many people has issues with the formatting of the final flag which is why they included the 0s and the DDMMYY format.
Anyway, if it was'nt obvious enough, the answer is the date of national day. The previous 3 mrt station codes actually comes together to form 08-09-25.
payalebar CC9 EW8
city hall NS25 EW 13
woodland NS9 TE2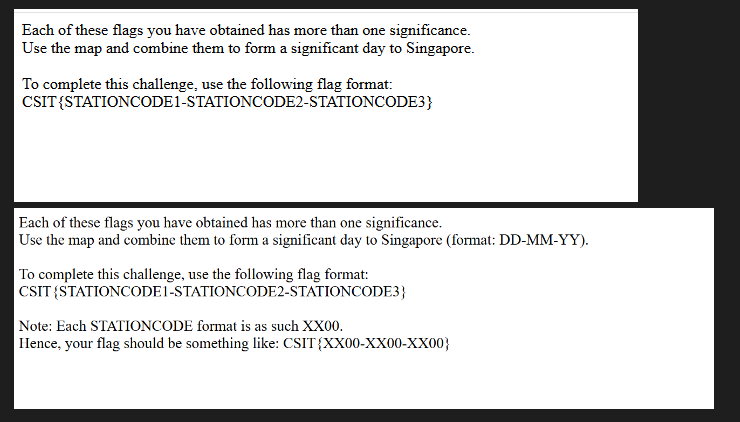
Thats all! Congrats on getting this far, or even reading this Walkthrough. I hope you had fun because this was a good break from studying OSEP. Till the next challenge, cya 🎉.
Sidenote: TISC Challenge is coming soon I believe, so do keep a look out if you're interested in participating.